Business under fire
Over 40 million new variations of malware were identified in 2015 – per quarter! Just the amount of ransomware – software that encrypts data and blackmails the owner to pay for the decryption key – has doubled since 2014 to more than 5 million (source: McAfee Threat Report 2015).
Even more dangerous are targeted attacks triggered by hostile competitors and shady government agencies. In the so-called “darknet” well organized hacker-teams offer their services, to wreak havoc on competition, disrupt operations and steal intellectual property.
Protecting what is most valuable
Applying maximum protection throughout the entire IT infrastructure is neither inexpensive nor trivial. Security experts recommend building up a strong baseline security giving special focus to key assets – the “crown jewels” of the company.
The obvious thing to protect is valuable data, like construction plans and manufacturing procedures for new products or secret know how.
What is less likely to be in focus is the infrastructure itself. However, it is the processes – and the platform they run on – which are essential. Whether it is finances and accounting, human resources, R&D data or CRM: ERP-software like SAP is the backbone of every business. Working without this tool is virtually impossible in almost every aspect of operations. All important information is gathered here. All processes are coordinated here. There is no IT system in which crucial information is available as condensed as is here. That makes SAP a prime target for severe attacks.
Top risks for SAP systems
In fact organizations run their most critical business processes on SAP, with employees, external consultants, providers, suppliers and others getting access and accounts trusted with permissions, rights and privileges within SAP landscapes to perform specific tasks and ensure business operations.
SAP access combined with other tools provided to users, can also be used to perpetrate fraud, harvest intellectual property, or sabotage operations. The scenario becomes even more frightening when we take into account the different, potentially vulnerable, endpoint devices accessing SAP.
SAP landscapes in large organizations can be highly complex, comprising thousands of users and roles, countless processes spanning the entire enterprise and massive infrastructure requirements. This complexity leads to a number of potential and apparent weaknesses – to name just a few:
- Audits imply time-consuming procedures and hence are only carried out on scarce occasions.
- Regularly checking for Segregation of Duties (SoD) does not help discover attacks immediately, nor prevent them.
- Customization oftentimes adds millions of lines of code to the core system, introducing a massive potential for vulnerabilities.
- ABAP-Code is a source of vulnerabilities in itself.
- Patching remains a problem: unplanned outages of a crucial system like SAP cause significant costs – a risk that not everyone is willing to take for applying a patch. On the other hand this can cause known vulnerabilities to remain intact for years.
Securing and monitoring SAP
Signature-based security systems like classic anti-virus software are incapable of stopping modern attacks. Even ambitious providers of such software have a hard time keeping up with the exponentially increasing number of malware fished from the web each and every day. And those are only the ones captured by various security labs around the globe.
Especially targeted attacks, using sophisticated malware tailored to a specific target, slips by any conventional system without being noticed.
Modern security systems directly monitor what is going on in the network to identify attacks based on behavior instead of signatures. To utilize the enormous number of security relevant events in an IT-landscape, Security Information & Event Management systems (SIEM) are applied. Modern SIEM solutions can automatically analyze and correlate more than 25.000 events per second (EPS).
Suspicious occurrences that are typically due to malware activities can thus be identified quickly. The SIEM records, normalizes, aggregates and correlates log events from various sources (Cross-Device & Cross-Vendor Data). This way it is possible to identify among tens of thousands of events those that pose an actual threat to critical business applications and data.
Unfortunately, SAP and other business applications do not integrate well with SIEM systems. Most SIEM solutions can barely read the Security Audit Log (SAL). The SAL in itself is not an exhaustive source of relevant information. For example it is possible to detect a change in user rights, but it is impossible to track what exactly has changed.
There is a severe information gap integrating SAP systems in SIEM solutions, which we call the SAP-SIEM-Gap. Closing this gap requires four major steps to be performed:
- Knowing, accessing and extracting all relevant data from a heterogeneous SAP landscape
- Providing this data in a standardized way to an attached SIEM for further processing
- Provide interpretational use cases for the SIEM to monitor what happens in SAP, and
- relating this information to what happens outside of SAP
Rules of correlation, graphical visualizations and dashboards or meaningful reports, based on DSAG-guidelines can not be provided by any SIEM.
The challenge is the highly interdisciplinary knowledge necessary to bridge the SAP-SIEM-Gap. To SIEM providers SAP is merely one of many data sources. This is where agileSI™ enters the game, connecting both worlds.
SAP security as a priority
Ensuring the security of IT systems, including SAP, is now one of the most important challenges faced by system administrators. Good practices worked out at BCC (now All for One Poland) over several years of rendering SAP and IT outsourcing services are now provided by us in the form of consulting services for the organizations that want to verify or improve the level of security of their own systems. We provide assistance in all aspects of security – from audits and penetration testing through procedural issues and training to the technical implementations. The completed projects include the implementations of the information security management system compliant with ISO 27001; verifications of the security of networks, operating systems and applications, and detection of vulnerabilities to social engineering attacks.
The cooperation of BCC with agileSI™ is a new chapter in building a comprehensive approach to the IT security management, in which the key role is played by SIEM (Security Information and Event Management) systems. The agileSI™ software (Security Intelligence for SAP Systems) is a bridge connecting SAP systems with SIEM systems. The agileSI™ software enables our customers to monitor in real time the SAP system security incidents in SIEM systems. The deployment projects carried out jointly with customers allow for the implementation of use cases, which focus the security monitoring on the most critical processes and data in SAP systems.
The new offer of BCC addresses organizations with strong emphasis on the security of processes and data in SAP systems. Teamed up BCC and agileSI™ combine decades of SAP know how and hosting with profound knowledge of top security and SAP/SIEM integration.
As part of the cooperation, BCC offers sales, implementation and customization of the agileSI™ solution, including any necessary work in the SAP environment.
Dariusz Kurkiewicz, SAP Basis Implementation Team Leader, All for One Poland
Holistic approach beats a single solution zoo
Among companies, a bulk of solutions is used to enhance various aspects of SAP security.
SAP GRC Access Control for example helps with the definition and implementation of a role based permission concept and helps with monitoring and auditing permissions. However it is incapable of monitoring sources like the SAL, system log, table logging or configuration parameters.
For code scanning there are tools like Fortify, a solution supplied by Hewlett Packard Enterprise. The reporting tool RSECNOTE can provide a list of applied and yet open security patches.
However none of these tools can cover more than a select number of aspects.
A totally different approach is provided by agileSI™. Right from the beginning, design was focused on providing real time monitoring (agile) through integration with top of the line SIEM systems (Security Intelligence, i.e. SI).
agileSI™ uses a 3 tier architecture, based on a central core, an agent for every SAP module to be monitored, and the applied SIEM system. The solution functions as an interface, extracting all necessary data from the SAP system landscape applying filters and additional logic before providing it to the SIEM solution.
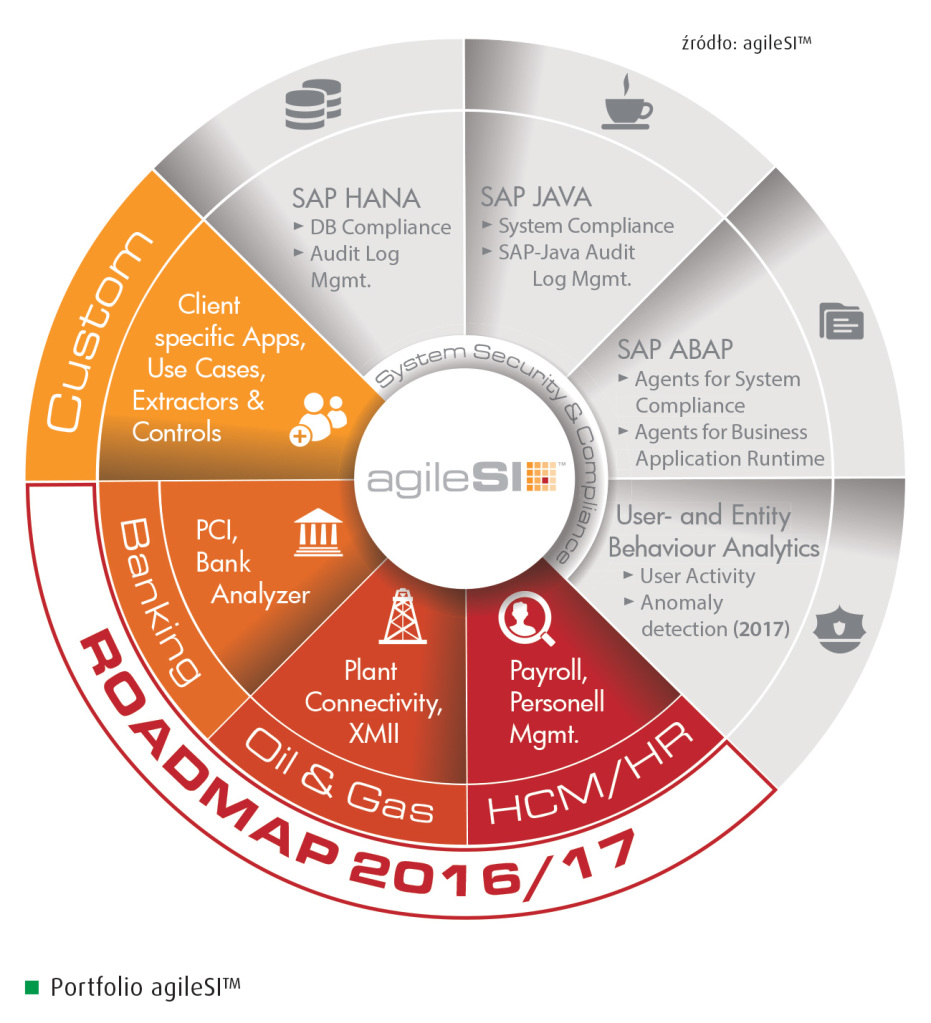
Agents continuously collect information and are centrally managed and configured. In the core, data is preprocessed and formatted for transition to the SIEM system of choice. Core and agents can be comfortably controlled using a single front-end. This way a highly flexible, adaptable and extendable extractor front-end is provided, which is capable of monitoring even customer specific tables and transactions.
As far as SIEMs are concerned: integration is available for HPE ArcSight ESM, IBM/QRadar, LogRhythm, LogPoint and Splunk. A substantial security analytics pack is provided: SAP security recommendations and practical experience from pen testing as well as DSAG guidelines were cast into code and are provided as preset tests and reports. Additionally industry-specific content packages are under development e.g. for banking & finance, oil & gas and the pharmaceutical industry.
Surveillance includes all aspects of SAP, like SAP ABAP, SAP HANA and SAP JAVA. As an additional security factor, user behavior analytics (UBA) will be added, which allows detection of hacked accounts, and identification of negligent or malicious behavior of users.
Benefits of agileSI™
The benefits of a symbiosis between SAP and SIEM are manifold. Web-based interfaces and access to the SIEM offer various stakeholders insights into the state of the SAP system. Along with IT managers, auditors, examiners und SAP administrators, it is the analysts in the Security Operation Center (SOC) that profit the most.
Some examples of the most common use case scenarios:
Compliance monitoring of security parameters:
- Table settings
- Profile parameters
- Security patches
Monitoring security relevant events in SAP:
- Security Audit Log, System Log, Table Change Logging
- Change record for roles and user data
- Transport Management System STMS
- Monitoring of transactions, applications, reports and functional modules
- Gateway settings and logs
Correlation (cross-event and cross-device) of SAP data mentioned afore with events like:
- Messages from security devices (e.g. application firewalls, malware detection systems)
- Identity management systems
- Database logs
- System- and network events
Some examples of important detection use cases:
- Server monitoring: Surveillance of crucial SAP servers
- Access monitoring: Alerting when two users are logged into SAP on the same terminal or repeated login of a user from different countries in a suspiciously short time
- Monitoring of critical users: permanent tracking of special accounts (firefighter accounts, SAP-standard users like SAP*) with situation based alarming when these accounts are used
- Automated incident response: automatic login blocking from malware infected Clients to SAP using the REST-API of an application firewall (e.g. ending the TCP-Session, log level rising of the user account or temporary lockdown of the account)
- Use as a framework: centralized automatic real-time monitoring of client specific applications and data
- Workflow integration: configuration faults and critical Events in SAP can immediately be passed on into a ticket system or via e-mail
- Forensic analysis: Access and transactions are tracked and recorded, so in case of suspicion, detailed investigations are possible.
agileSI™ as a managed service
agileSI™ fits perfectly into a SIEM landscape to close the gap with SAP. But what if there is no SIEM?
In particular, smaller companies might not be interested in setting up a SIEM system at this point. After all it is not sufficient just to buy a set of hard- and software. Without a skilled team it is impossible to benefit from a SIEM system. The system has to be administered, operated and continuously adjusted to changing threat situations and company needs. Skilled SIEM experts and cyber analysts are inevitable for threat vector modeling, attack analysis and triage as well as response operations.
Good, trustworthy personnel in this field might be excessively hard to find.
Conveniently SIEM is offered as a managed service by companies like BCC and iT-CUBE SYSTEMS AG. The operation and administration of the SIEM including soft- and hardware (as well as agileSI™ if required) would be outsourced to the service provider. The network, including all SAP systems is then remotely monitored.
The required effort in this case is remarkably small, while the cost remains a plannable figure.
As a bonus managed service providers can usually guarantee a 24/7 service for system monitoring, attack detection, analysis and response. After all, hackers are not limited to the usual business hours either.
Conclusion
Whoever wants to continuously monitor and control the security state of their SAP landscape in real time, while focusing on intelligent attack detection combined with enormous flexibility and the ability to trigger immediate defense mechanisms should think about an SAP-SIEM-Integration using solutions like agileSI™ as a bridge in the very near future.
agileSI has been acquired by LogPoint company in 2020. Go to LogPoint website for more information.

