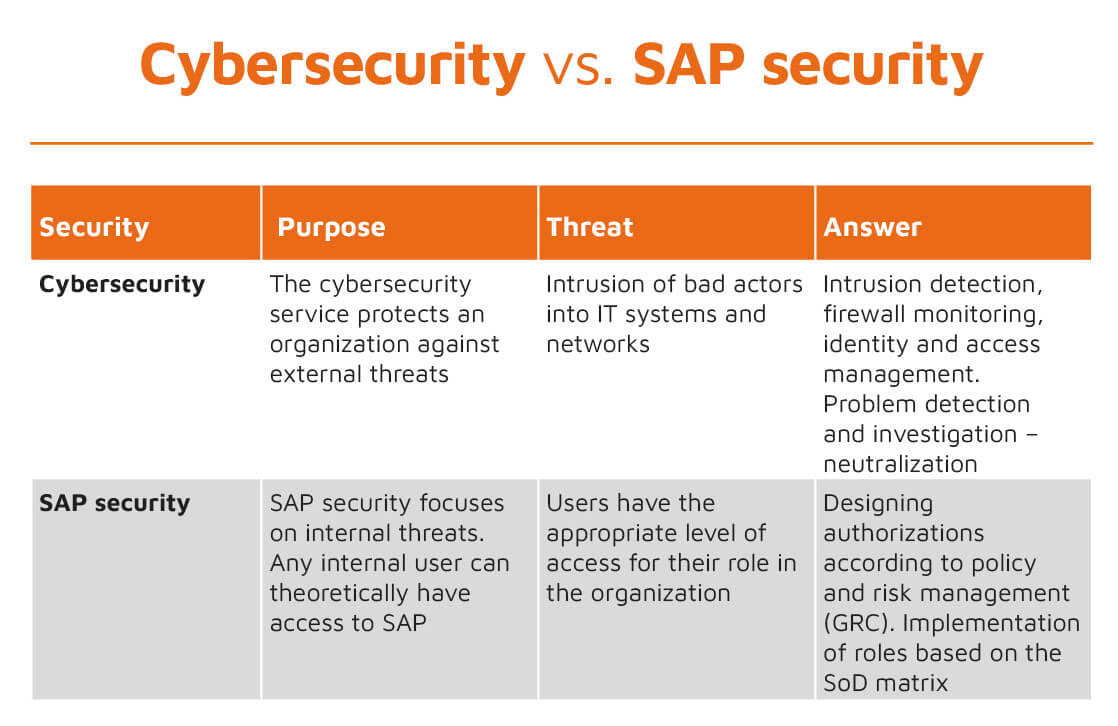
SAP security is a balancing activity that includes all the tools, processes and controls put in place to restrict user access to the SAP environment. A similar methodology is used when designing and implementing comprehensive security measures across the entire organization. However, when designing a cybersecurity system for SAP, it is important to consider some differences between cybersecurity, which focuses primarily on protection against external threats, and SAP security, which focuses on internal threats.
The main difference is that, by design, any user in an enterprise’s network can use SAP applications, and users have an access level appropriate to their role as defined according to risk management and control (GRC) procedures. Activities related to protection against attacks, on the other hand, focus on keeping hostile actors out of an enterprise’s network and systems. These mainly include intrusion detection, firewall monitoring as well as identity and access management (IAM).

Pillars of SAP security
Protecting data, procedures, user identities
SAP systems are a special case where stringent security and threat protection measures must be applied. They are filled with data that is attractive to hackers, such as confidential information, e.g. financial records, procedures, personal data of customers, bank account data and intellectual property. Data from the system can also be used for identity theft, fraud, industrial and international espionage, as well as phishing operations in which hackers trick employees into transferring funds to foreign bank accounts. We outline the key pillars on which an effective SAP cybersecurity system should be based.
SAP systems are a special case where stringent security and threat protection measures must be applied. They are filled with data that is attractive to hackers, such as confidential information, e.g. financial records, procedures, personal data of customers, bank account data and intellectual property. Data from the system can also be used for identity theft, fraud, industrial and international espionage, as well as phishing operations in which hackers trick employees into transferring funds to foreign bank accounts. We outline the key pillars on which an effective SAP cybersecurity system should be based.
Start with an audit
Every organization is different, uses different IT systems and is based on different business processes. For this reason, the processes taking place in the area of security should begin with an internal IT audit, preferably with the participation of an entity specializing in such projects, which will help determine the needs of the organization, classify the elements at risk, assign them the appropriate priority and level of protection, taking into account the value of the thing considered as information. The effectiveness of the design process is affected by several factors, such as:
- divergent IT goals vs. business objectives,
- lack of strategic security decisions,
- no process owner,
- complexity of the security system being designed,
- lack of scalability of the solution as the organization grows,
- lack of project documentation, progress control and indicators confirming the achievement of the goal.
People
No less important, in fact, the most important element of the project is the people. A flexible, energetic and, above all, committed and competent team significantly affects the level of security of SAP systems already at the design stage and guarantees the final achievement of the set goal. A well-prepared team includes people responsible for decision-making, technical people – responsible for the implementation of individual systems, functional people – responsible for the business aspects of the application’s operation, and people from the security area of IT systems, including SAP. When preparing the team, the following must be considered:
- the size of the team depending on the importance, size and urgency of the project,
- knowledge transfer regarding functional and technical requirements,
- communication between team members,
- progress control.
Data security
The team’s priority is to ensure the secure storage, processing and transmission of data, that is, to protect it from intentional or accidental disclosure, modification or destruction. The most important attributes of the designed system are confidentiality, authenticity, integrity, availability and reliability. In order to ensure them, a variety of protection methods and measures must be applied in parallel. This generally comes at the expense of system functionality and efficiency. Therefore, when designing security, it is necessary to consider several main factors that affect the actions taken:
- method and control of access to SAP applications,
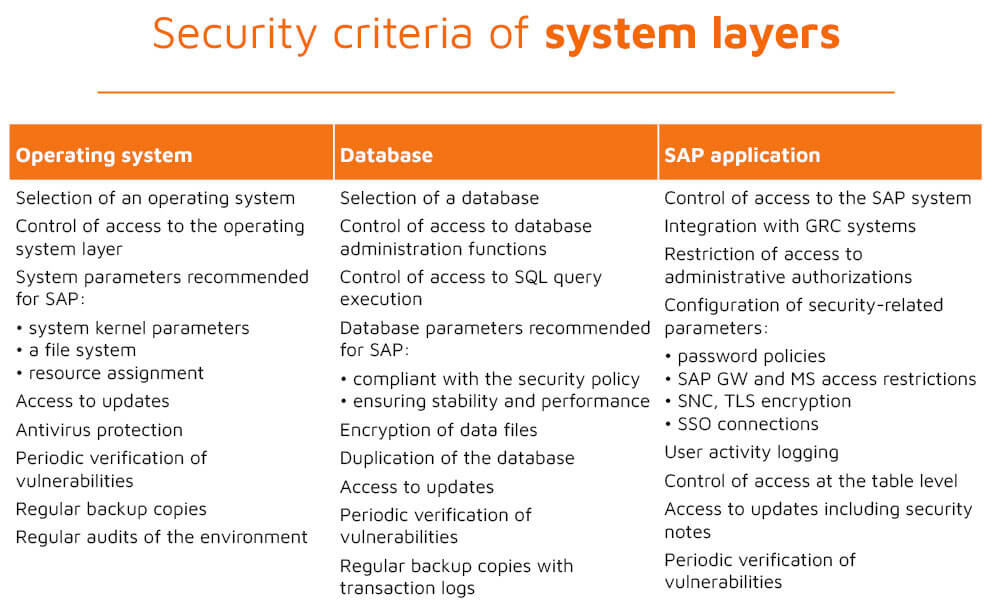
- security of the different layers of the system: a hardware platform, an operating system level, a database level (encryption, backup), an SAP application level,
- the location of the systems (cloud, on-premise) along with the rules of communication between them,
- “firefighters" emergency access rules.
Access control
A special element of security and data confidentiality is informed access control, which must be seamless so that users are not blocked in the workflow. Users must be allowed access to perform required work activities while preventing them from viewing or modifying data to which they are not authorized. In the aforementioned aspects, SAP application security is focused in three areas:
- access control performed by unique user identification,
- data security ensured by restricting access to data by role,
- security of the application itself through patch management, control and management of privileged access (no administrative access for unauthorized persons).
Unique user identification involves granting access to the system only to the user who identifies his or her identity during the login process by providing a username and password or using a method extended by another authorization component, e.g. an SMS code. After correctly logging in to the system based on the roles assigned to users, the next stage of verification is performed to allow access to the collected data.
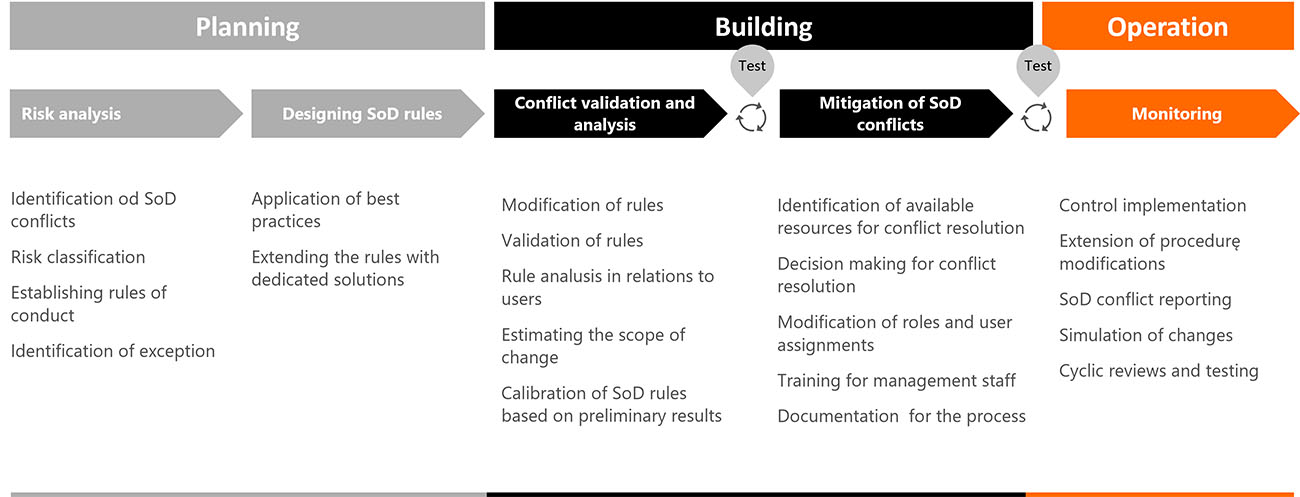
Such a method of access control forces the project team to apply special care and attention during the preparation of the concept and implementation of the authorization matrix, taking into account the segregation of duties. Before performing this action, an authorization analysis should be carried out. The reason for such an analysis is to reduce one of the basic internal risks for the organization, i.e. too much access to the system for a single user.
A separation of duties (SoD) conflict arises when one user can perform activities in the system or between systems that should be separated and performed by at least two employees due to the company’s internal control, security of company processes, good business practices, and legal regulations. The process of introducing the separation of duties and managing SoD conflicts is a continuous process.
Before the system goes live, a whole series of tests should be carried out to confirm its readiness to provide services. Security aspects based on the authorization implementation model responsible for the level of selectivity of data access should also be an element of the tests. In particular, for the SoD model, elimination tests must be carried out to confirm the rule that one user cannot carry out the entire process path, e.g. a user with the authorization to set up suppliers in the system should not have the authorization to pay them.
Application development
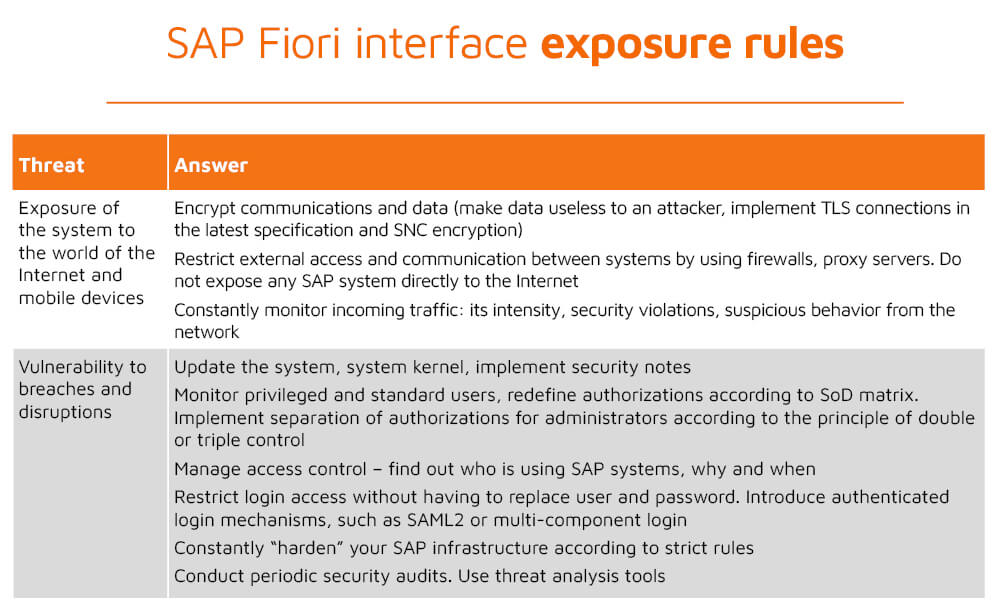
Another variable to consider at the design stage and during risk management is the SAP application development itself. Originally, the system environment was fairly isolated, but with the rapid development of the Fiori user interface, and thus access to it from the wide world of the public Internet and mobile computers, the area of attack on the application has also increased. Attackers now have many more points of vulnerabilities to exploration.
An unprotected Fiori can introduce new vulnerabilities, actually exposing the entire environment to threats due to flawed interface security measures. This is compounded by the fact that the point of entry into the system is almost irrelevant in today’s cyberthreat landscape. Increasingly, attackers are using a broad spectrum of AI-based automated bots to probe corporate networks for security vulnerabilities. Automated attackers can find their way into networks and hide their activities until they are activated by supervisors. Mitigating risks to SAP systems and the valuable data they contain requires a number of SAP Fiori security best practices to be adopted.
System hardening
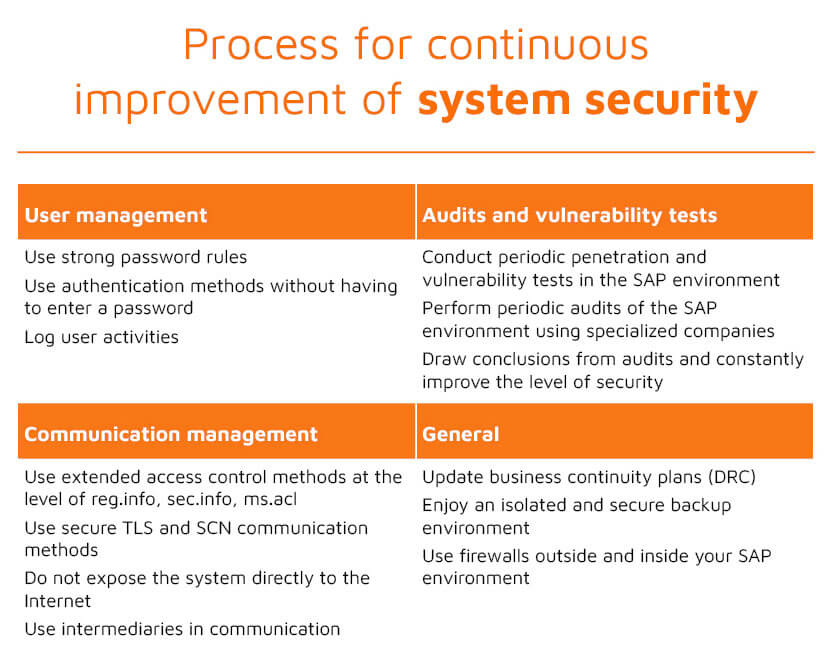
The main objective of the “Secure SAP" project is to carry out threat balancing activities, as a result of which we acquire a well-secured SAP environment that guarantees business continuity, a secure and optimal configuration. This process is called system hardening. It involves making changes to the systems to minimize the risk of external attack and the outflow of malware.
When taking action, special attention should be paid to its subsequent follow-up consisting in continuous monitoring of the environment, audits, drawing conclusions and introducing improvements. A well-documented security audit will provide the organization with a prioritized list of issues and tasks required to eliminate threats.
Integration of cybersecurity tools
Security measures in SAP applications work effectively when control mechanisms built in SAP are well integrated with the organization’s broader cybersecurity and GRC functions. An example of such integration would be the use of Identity Management (IDM), an SAP solution integrated with Microsoft Active Directory. This way, if an employee leaves the company, he or she will also be locked in SAP. It is very common for an employee’s user to remain active in the system after the end of work.
It’s also good practice to integrate the SAP system with an external monitoring system, particularly one that can analyze security logs, looking for incidents and violations (e.g., a SIEM type).
The GRC solution, in turn, analyzes what users can and do in the system, and then creates policies to eliminate risks and meet compliance requirements. SAP’s security department implements these principles – on a daily basis – for example, by provisioning new users and analyzing signs indicating that a system is not operating according to GRC requirements. GRC software helps both the GRC team and the SAP security team do their jobs more efficiently and effectively. A well-designed security system running smoothly every day informs process owners and enables them to adapt to changes in the organization