Multi-Factor Authentication (MFA) is a component of application access process management that requires users to confirm their identity using at least two different verification factors (2-Factor Authentication 2FA). If one of the factors is compromised, such as by stealing user login credentials, then the attacker will have at least one more barrier to overcome before gaining access to the system.
The use of multiple authentication factors to prove identity is based on the assumption that an unauthorized party is unlikely to be able to provide all the factors required to gain access. If at least one of the factors is missing or incorrectly provided during an authentication attempt, the user’s identity is not established with sufficient certainty, and the resource protected by multi-factor authentication remains inaccessible.
The most common categories of authentication factors are:
- Something you know. Usually a password, PIN or answers to a set of security questions that only a specific person knows. To use this factor, the user must correctly enter the information required by the application;
- Something you own. Usually a smartphone, a secure USB key or a one-time code generator. Currently, the most common choice is an authentication application on the user’s phone for generating One Time Password (OTP) keys;
- Something you are. Usually biometric data, such as fingerprints, retinal scan, facial or voice recognition.
In order for the authentication process to work properly, the user is always required to present at least two authentication factors from two different categories.
Cyber-attackers most often take advantage of employees’ ignorance or credulity to bypass software or hardware resistant to various types of attacks. In many situations, unaware employees are ready to reveal information that may be useful in an ongoing attack. In order to be able to respond appropriately to such attacks, employees should be aware of their occurrence and should know what form they can take and where they can encounter them.
Authentication in SAP
Aware of the threats, SAP has incorporated multi-factor authentication mechanisms into its software to help IT departments counter such attacks. Regardless of the solution’s location, be it an on-premise deployment or a cloud deployment at one of the hyperscalers, it is possible to implement two-factor authentication. However, the available authentication factors and solution deployment methods vary.
By default, NetWeaver ABAP and Java solutions do not support the MFA mechanism. Multi-factor authentication can be configured after implementing SAP Single Sign On 3.0, a separately licensed product. The said product allows for using the One Time Password login module (TOTPLoginModule) in NetWeaver Java solutions. The module provides several methods for generating a one-time password and making it available to users:
- An access code generated by a mobile authentication application (e.g., SAP Authenticator, Microsoft Authenticator). Required installation of the mobile application on the user’s phone;
- A random password sent via SMS, email or other channel. Configuration designed for users who cannot install a mobile authentication application. The password can be sent to users via SMS or email;
- An external access code generated by a third-party access code provider.
The configuration applies to access codes from a third-party provider (e.g., RSA SecureID) that must be verified before user authentication. For authentication purposes, developers must implement a policy script written in JavaScript.
After this type of configuration, e.g. in the SAP NetWeaver Portal application, all employees of the organization will be able to log in with a one-time password in combination with the traditional user and password login or SAP Logon ticket login.
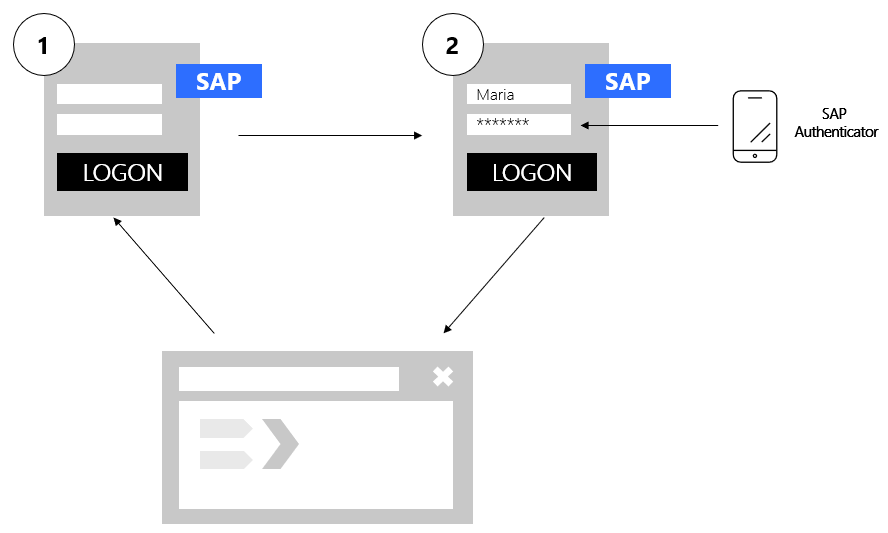
SAP application login process: 1. Entering a user name and password; 2. Entering the generated code from SAP Authenticator or other applications
In the SAP world, the SAPGui login client is still very popular. This client does not support direct multi-factor authentication capability, but supports the process through a non-direct configuration based on the OTP login module allowing for obtaining an x.509 certificate, which, combined with the configuration of SNC communication between SAPGUI and the application server, provides two login factors.
WebGui, Fiori or other browser-based user interfaces use a standard based on the SAML 2.0 (Security Assertion Markup Language) protocol in most configurations. This is one of the most popular Internet protocols used every day by millions of Internet users to easily log in to applications and online services.
In the authentication process, the identity provider (an IdP system, e.g. SAP Business Technology Platform Identity Provider, Azure Active Directory) passes the authentication token to an application known as a service provider. SAML enables the service provider to operate without performing its own authentication and identity transfer to integrate internal and external users. This allows security credentials to be shared with the service provider on the network, in the application or service, as well as in cross-domain communication between the public cloud and other systems. By adding a second authentication factor to the configuration, e.g. a one-time code from the application or biometrics, we obtain a multi-factor configuration. As a result, during the login process, the user will be asked to log in with the data provided by the IdP, and in the second step – to enter a generated code from the application or a fingerprint scan.
Similar multi-factor authentication capabilities are also provided by the SAP Business Technology Platform (SAP BTP), a cloud platform. The platform combining data, analytics, artificial intelligence, application design, automation and integration in one unified environment enables the use of SAML and TOTP authentication mechanisms along with distribution via SMS or e-mail.
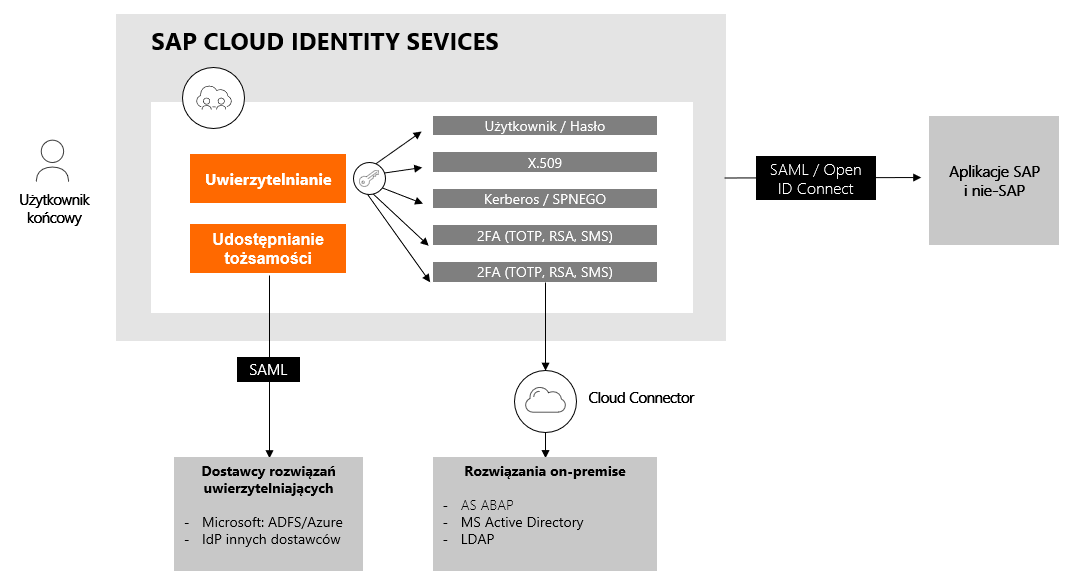
Multi-factor authentication on the SAP Business Technology Platform
Zero Trust
It is estimated that most breaches originate from employees’ workstations. Therefore, due to the increase in the popularity of remote work, securing access to an organization’s sensitive data or data protected by law requires the introduction of an additional layer of identity confirmation. This allows for the implementation of the Zero Trust security architecture, which significantly reduces the vulnerability to social engineering attacks against employees, guaranteeing better control over access and compliance with security regulations and standards, such as GDPR or ISO 27001.
Modern SAP solutions supported by MFA also guarantee a high level of protection of company resources. Their implementation can thwart many security breach attempts, as well as protect the company from the costs associated with the need to restore or set up systems anew.

